Cyber attack hits global businesses and Ukraine government

Roula Khalaf, Editor of the FT, selects her favourite stories in this weekly newsletter.
Some of the world’s largest companies including WPP, Rosneft, Merck and AP Moller-Maersk have been hit by a large-scale cyber attack that also took critical government and bank infrastructure in Ukraine offline on Tuesday.
Computers, ATMs and supermarket checkouts were among the devices debilitated by a ransomware attack that bears similarities to WannaCry, which infected hundreds of thousands of computers in 150 countries last month, according to cyber security experts. No one has yet claimed responsibility for the latest attack.
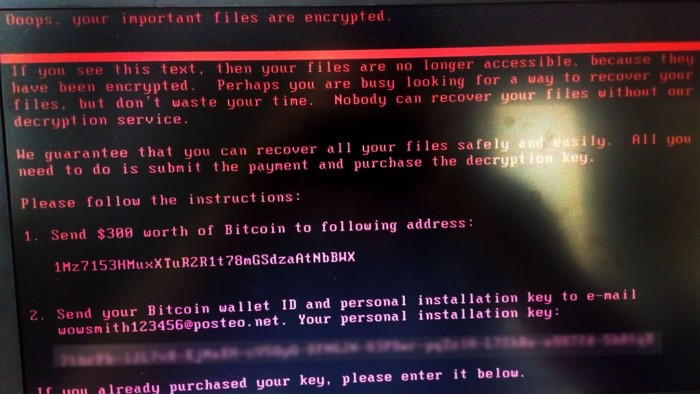
Hackers shut down access to computers and displayed a message demanding a $300 ransom from users, payable in bitcoins. Cyber security experts have identified the attackers’ bitcoin account, which suggests they have received about 20 payments so far.
Interpol said it was “closely monitoring” the attack and liaising with member countries. The US Computer Emergency Readiness Team, which responds to major cyber threats, discouraged individuals and organisations from paying the ransom, saying there is no guarantee that this would result in access being restored.
Ukraine’s cyber crime police unit warned that updating functions in a domestic accounting software package known as M.E.doc was being used as a conduit to wage the “virus attack on Ukrainian companies”. But the attackers appear to be using many ways to enter systems, including phishing emails.
Beau Woods, deputy director of the Cyber Statecraft Initiative at the Atlantic Council, a DC-based think-tank, warned that the virus looked more powerful than WannaCry.
He said there were “more severe implications” because it was structured to spread more quickly and run effectively on several different versions of Windows. Most worryingly, it could have been created without the ‘kill switch’ which slowed the spread of WannaCry.
“If there is no kill switch, then this could rampage for months,” he said.
Other companies affected included Saint Gobain, Evraz, Russia’s second-largest steelmaker, and DLA Piper, the law firm. The attacks were widespread in Ukraine, affecting Ukrenergo, the state power distributor, and several banks.
Pavlo Rozenko, Ukraine’s deputy prime minister, tweeted a photo of a computer screen. “The network is down,” he wrote.
Some security researchers said that the attack used the same flaw exploited during the WannaCry breaches. That would make systems that have not been updated since that attack particularly vulnerable.
Mikko Hypponen, chief research officer at F-Secure, a Finnish cyber security company, could not confirm that attack came from the hackers who were behind WannaCry. But he said they were using the same vulnerability, EternalBlue, which was exposed in a dump by a group called the Shadow Brokers and thought to be stolen from the US National Security Agency.
“So WannaCry was not enough of a wake-up call. You would think everybody would be patched by now,” he tweeted.
Rosneft, Russia’s largest oil company, said it had moved to a reserve oil production system after a “powerful” hacking attack took down its website and that of its subsidiary Bashneft. The company said it had contacted authorities and warned on Twitter that “distributors of false, alarmist messages will be treated as accomplices of the organisers of the attack and held accountable”.
Computers and internal intranet and wifi networks in the Russian company’s Moscow headquarters were disabled on Tuesday, a company source told the FT on condition of anonymity. The person added that no core business functions had been affected.
“Thanks to the fact that the company switched to a standby system for managing production processes, neither the production nor the preparation of oil was stopped,” Rosneft told the Financial Times.
WPP, the world’s biggest advertising group, said on Tuesday: “IT systems in several WPP companies have been affected by a suspected cyber attack.” The website for the holding group, which owns agencies such as Group M and Burson-Marsteller, was unavailable.
Saint Gobain, the French construction group, was also hit. A company spokesperson said: “As a security measure and in order to protect our data, we have isolated our computer systems.”
————————–
Companies hit: some big names affected by the cyber attack

● AP Moller-Maersk: world’s largest container shipping company
● Rosneft: Russian energy company
● WPP: world’s biggest marketing services company
● Merck: US pharmaceutical company
● Saint Gobain: French construction group
● DLA Piper: one of the world’s biggest law firms
● Reckitt Benckiser: UK consumer goods group
● Evraz: Russia’s second largest steelmaker
————————–
Russia’s central bank said on Tuesday that several lenders had been hit by cyber attacks, without providing their names.
The bank had recorded “computer attacks aimed at Russian lending institutions . . . [and] infection of information infrastructure facilities”, its press service told news agency Interfax. It added that its cyber security division was “working with credit organisations to eliminate the consequences of detected computer attacks”.
Ukraine’s central bank said Ukrenergo, the state power distributor, and several Ukrainian banks had been attacked by an “unknown virus”, but declined to share further details.
Group IB said that other victims in Ukraine included PrivatBank and Oschadbank, two of the country’s largest state-owned banks, the country’s three main mobile operators, Kiev’s airport and metro system, and local offices of foreign companies including Nivea, Mars and Mondelez International.
The virus appears to have evaded many versions of anti-virus software, with VirusTotal, which tracks what each vendor can detect, identifying only a couple of vendors that blocked the virus.
Sean Sullivan, a security adviser at F-Secure, said companies should warn their human resources departments not to open any attachments, as previous versions of Petya, a ransomware that somewhat resembles this malware, have targeted recruiters receiving CVs.
The variant of the ransomware appeared to have been made on June 18, nine days ago, according to a time stamp analysed by a researcher for Kasperksy Labs.
The company said the vast majority of infections so far were in Ukraine, followed by Russia, Poland, Italy and Germany. However, attacks in the US emerged as people started their days and logged on to their work computers.
Group IB said the Petya virus’ code had previously been used to cover the tracks of an online criminal gang thought to be behind hacking financial institutions and cash machines in Russia and eastern Europe.
Reporting by Max Seddon and Henry Foy in Moscow, Hannah Kuchler in San Francisco, Roman Olearchyk in Kiev, Daniel Thomas, Mark Odell and David Bond in London
Comments