Websites built using the Anchor CMS may be accidentally exposing their database passwords in publicly-facing error logs, Dutch security researcher Tijme Gommers has discovered.
Gommers says that an attacker can navigate to the following URL and download a copy of the site's errors log, where in some cases, he may find the site's database password exposed in cleartext.
site-name.com/anchor/errors.log
1. Register on PublicWWW (https://t.co/DpQp4rtYEj)
— Tijme Gommers (@finnwea) February 18, 2018
2. Go to https://t.co/1mc01HdhaM
3. Pick a random blog created with AnchorCMS
4. Go to that-blog[dot]com/anchor/errors.log
5. Press [ctrl] + [f] and search for "password"
6. Database access granted pic.twitter.com/9JqxXQusLY
According to a PublicWWW search query, there are almost 500 Anchor CMS sites easily discoverable online based on their meta name attribute.
Bleeping Computer has found cleartext database passwords for a few of the sites included in the PublicWWW search results.
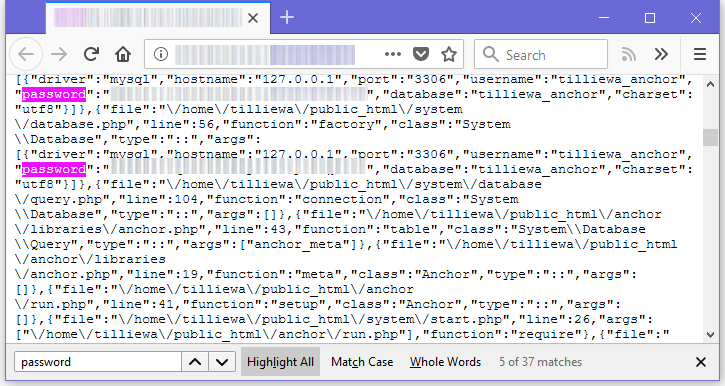
"The errors.log file is meant to be private, however, with the default install of AnchorCMS it is public," Gommers told Bleeping Computer in a private conversation.
Users may not be aware of the importance of this file, as the Anchor CMS docs do not include any special advisory for webmasters to hide this file from the public.
Anchor CMS logs database credentials in cleartext
But there is also an issue with Anchor CMS, which should not dump cleartext database passwords in the errors log, to begin with.
"This is the file that logs the error," Gommers said. "When MySQL errors are logged, it also logs the credentials in the arguments of the [SQL] trace."
One scenario when the error occurs is when there are too many concurrent connections to the MySQL server, a scenario that happens quite often to most websites at one point or another.
This means that if the errors.log is old enough, it will eventually include an entry for this error, and the MySQL database credentials, including username, password, and IP, all that an attacker needs to connect to a remote MySQL server.
How users can protect themselves
Gommers said he doesn't plan to report this bug to the Anchor CMS team. "I think its more of a DevOps issue," Gommers told us.
The security researcher believes site owners shouldn't be allowing access to the errors.log file in the first place.
"When you would want to keep using AnchorCMS I recommend disabling access to *.log files via the htaccess file for example," Gommers said. Furthermore, webmasters should be following this advice —limiting access to *.log files via htaccess— for all CMSes, not just Anchor.
An Anchor CMS developer was not available for comment on this article and security issue before publication, but the Anchor CMS team should also take note of this bug.
"To be a bit more safe I recommend changing the [Anchor CMS] code a bit to prevent getting the credentials in the log," Gommers says.
Further, adding a warning to the Anchor CMS docs about blocking access to the errors.log file would also help webmasters that are not aware of web security best practices.
But if the Anchor CMS team would like to go all-in, they can include a .htaccess file with the default installation package that blocks access to log files by default.
.jpg)

Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now