Large-scale credit card hackers back for the holiday season, ex-FBI investigator says

Notorious cybercrime group FIN7 appears to be back at work about a year after the FBI arrested three of its members, which dealt a major blow to the group’s activities.
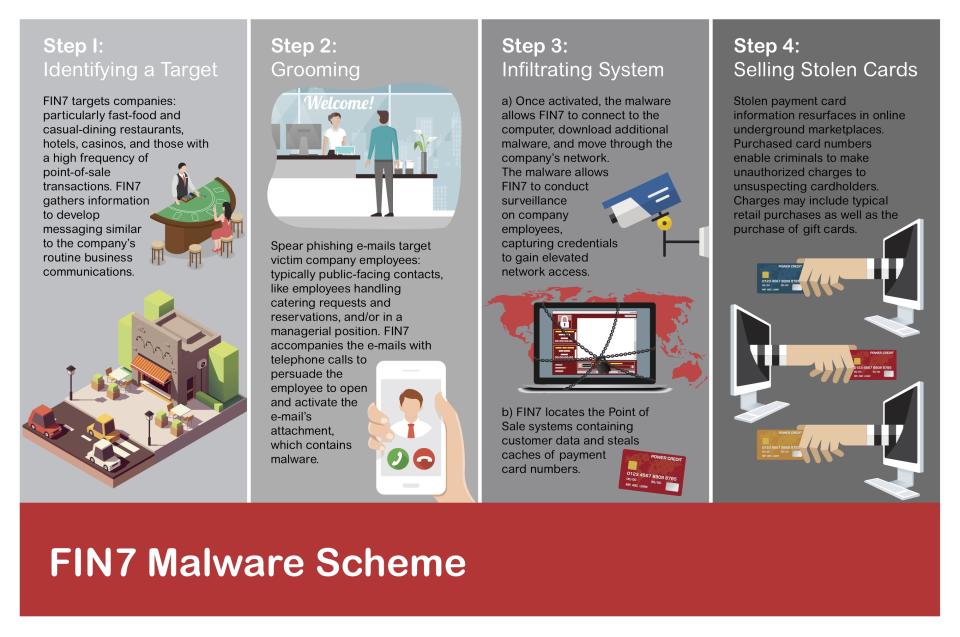
Between 2015 and the arrests in August 2018, FIN7 was responsible for a very advanced malware campaign that hit 100 companies in the hospitality industry, according to the FBI. Among the names that were publicly disclosed: Chipotle Mexican Grill (CMG), Chili’s (EAT), Arby’s, Red Robin (RRGB), Sonic, and Jason’s Deli.
FIN7 had been previously linked to data heists at Trump Hotels, Whole Foods (AMZN), Saks Fifth Ave and Lord & Taylor (HBAYF).
The group steals credit card data from point-of-sale terminals and other means. The data is then sold on the dark web, the internet’s black market. The cards are then used, costing financial institutions millions of dollars.
This week, cybersecurity group FireEye discovered a new piece of very advanced malware that it linked to FIN7, indicating the group has recovered and is back in action — posing a grave danger to retailers, hospitality groups, financial institutions, and consumers leading up to the holiday season.
“The group has definitely recovered,” said Randy Pargman, a former FBI senior computer scientist who left the Bureau a few weeks ago after a 15-year career, who continues cyber defense at Binary Defense. Pargman investigated the group at the FBI’s cyber task force in Seattle. “They seem to be actively recruiting more people to the group and have certainly been carrying out their operations and tools, including very sophisticated malware,” he said.
Most hackers use generic malware they buy on the dark web. And most companies of scale have anti-virus software that can detect and deal with these attacks. But FIN7 develops its own malware for its exclusive use, which renders anti-virus software inadequate for defense.
Hacking on an ‘enterprise scale’
FIN7 isn’t just a casual group of hackers in someone’s parents’ basement. The group is as advanced as many Silicon Valley startups, Pargman told Yahoo Finance.
“When FIN7 targets companies, they approach it on an enterprise scale,” he said.
The FBI is fuzzy on FIN7’s exact size, but it’s in the “dozens,” and there are several divisions that execute a specific function, much like a real company. There’s a research and development arm that figures out the best ways to phish and hack, a market research arm that identifies profitable targets for hacks, strategists who focus on tailoring the best approach, and a group that works on how to target and manipulate individual people via social engineering.
A lot of the work happens through phishing, often involving calling an employee of a company and pretending to be a customer. While the group is based in Europe and made up of many eastern Europeans, the American-accent issue isn’t a problem. Scammers on this scale can easily hire another type of dark web service: native English-speakers who will perform a script designed to manipulate the caller.
Once a person is manipulated to install something — which turns out to be malware — on their device without their knowledge, the malware can spread quickly, giving hackers control of more and more computers in the process. Then, that department hands off access to yet another group within FIN7, which finds and extracts the credit card records so FIN7 can sell them.
FIN7 has stolen around 15 million records in all, according to the FBI, which has led to around $100 million in fraudulent charges from the stolen credit card information. The amount FIN7 makes is considerably less, somewhere around $10 per card that’s sold — or less, if a dark web wholesaler is used, which is often the case, Pargman said.
A big factor in revenue is how fresh a card is and whether it has a zip code with it.
“We noticed they were making a lot of effort to steal the zip code along with the card number — and where the card was used,” said Pargman. This information is especially useful to fraudsters, as it enables the card to be used longer without detection. If it’s used in its owner’s zip code, it’s much easier to evade a bank’s fraud-detection measures.
What this means for retailers, hospitality groups, and consumers
With FIN7 appearing to return to activity, retailers that use a point-of-sale terminal should be on high alert.
“I think it’s really important for businesses in the retail industry to understand and have a profile of what type of attackers are up against them,” said Pargman. “What sort of goals they have and how they operate. The best frame of reference is to really think of them like a competitive business.”
Understanding that hackers have capital to invest and R&D teams is key, and that basic check-the-box cybersecurity protections may not be enough. A full-scale defense involves training employees in how to detect phishing emails and calls. Businesses that don’t take this seriously may find themselves as targets of another embarrassing and expensive data breach.
There isn’t much consumers can do to prevent the businesses they frequent from being hacked, but Pargman recommends having more than one payment card available, to read your own statements, and to be familiar with reporting requirements if you suspect fraud. U.S. federal law says consumers are not liable for transactions made with their stolen card number as long as it’s reported within 60 days (if the physical card is stolen, you have much less time).
However, Pargman says, it’s good to check your statement often and report as soon as possible: “If a watchful consumer can call and report a stolen number, that might be the one clue the financial institution needs to link together other fraud on other cards as well.”
-
Ethan Wolff-Mann is a writer at Yahoo Finance focusing on consumer issues, personal finance, retail, airlines, and more. Follow him on Twitter @ewolffmann.
Joining the top 1% just got more difficult, IRS data reveals
The downside to living longer: Running out of money
Social Security phone scams are now a greater threat than IRS scams
How to know if your next flight is on a 737 Max
The 2020 Social Security increase falls short
‘Flight shame’: A potential headwind for airlines in Europe
Read the latest financial and business news from Yahoo Finance
Follow Yahoo Finance on Twitter, Facebook, Instagram, Flipboard, LinkedIn, YouTube, and reddit.