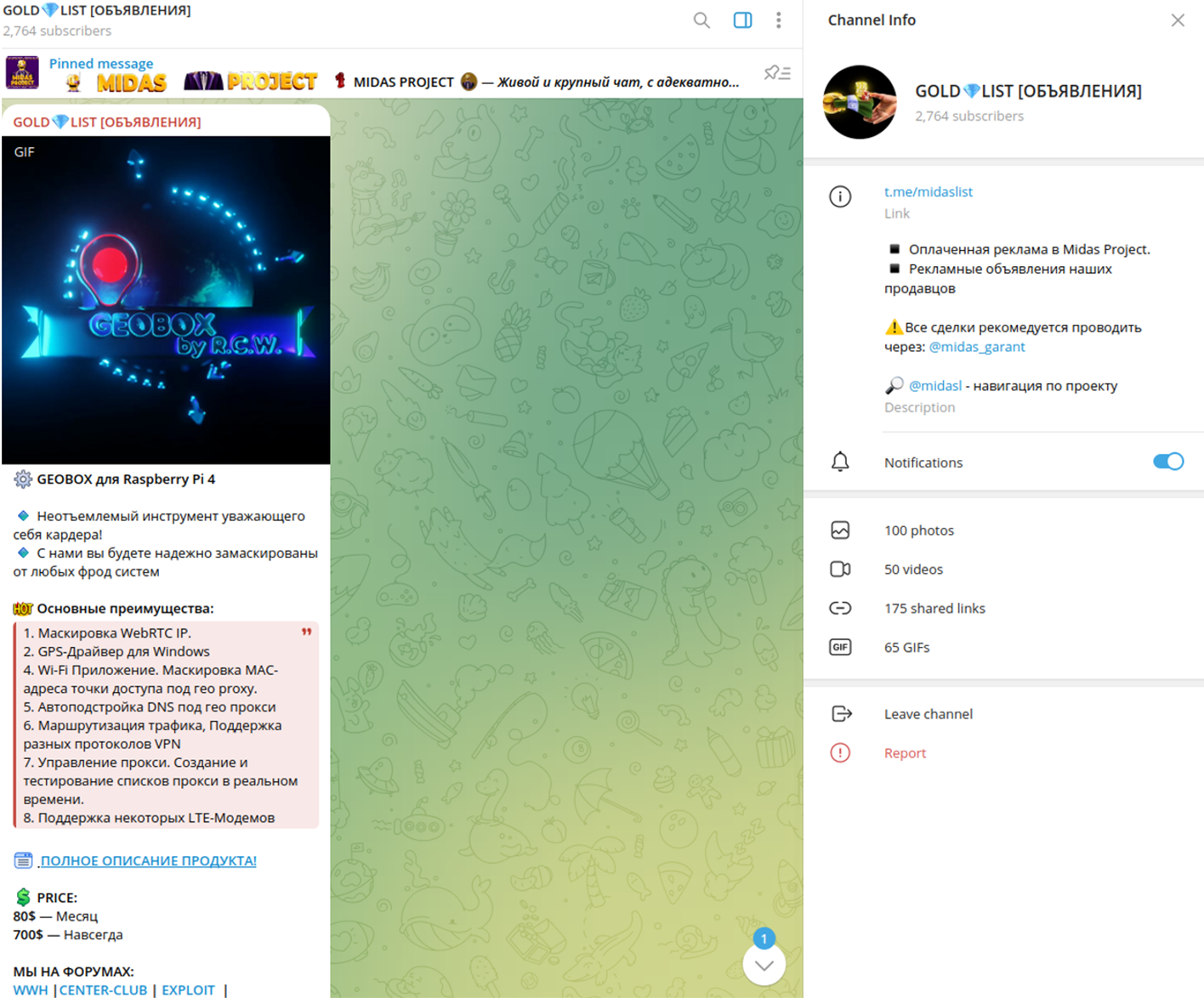
Cybercriminals are selling custom Raspberry Pi software called 'GEOBOX' on Telegram, which allows inexperienced hackers to convert the mini-computers into anonymous cyberattack tools.
GEOBOX is sold on Telegram channels for a subscription of $80 per month or $700 for a lifetime license, payable in cryptocurrency.
Analysts at Resecurity discovered the tool during an investigation into a high-profile banking theft impacting a Fortune 100 company.
"This discovery led to the acquisition of GEOBOX for more in-depth analysis. The malicious individuals utilized several GEOBOX devices, each connected to the Internet and strategically placed in various remote locations," explained Resecurity.
"These devices served as proxies, significantly enhancing their anonymity. This approach complicated the investigation and tracking process, especially since, by default, GEOBOX devices do not store any logs."
The researchers acquired the GEOBOX software for analysis and warned in a report today that it is a highly capable tool that can complicate law enforcement tracking and investigation.
Source: Resecurity
GEOBOX capabilities
The Raspberry Pi is an inexpensive yet capable system that can be bought for as little as $35, making it an excellent disposable tool for cyberattacks.
The device is extremely small and light, making it highly portable. This allows cybercriminals to move around in different locations with ease, connect to various internet access points, and obscure their tracks.
The small dimensions also make it easy to conceal, ideal in attack scenarios requiring proximity to the target without raising suspicion.
The GEOBOX Raspberry Pi software discovered by Resecurity acts as a cybercrime application suite focuses on fraud and anonymization, making it a potent tool for illicit online activities.
Source: Resecurity
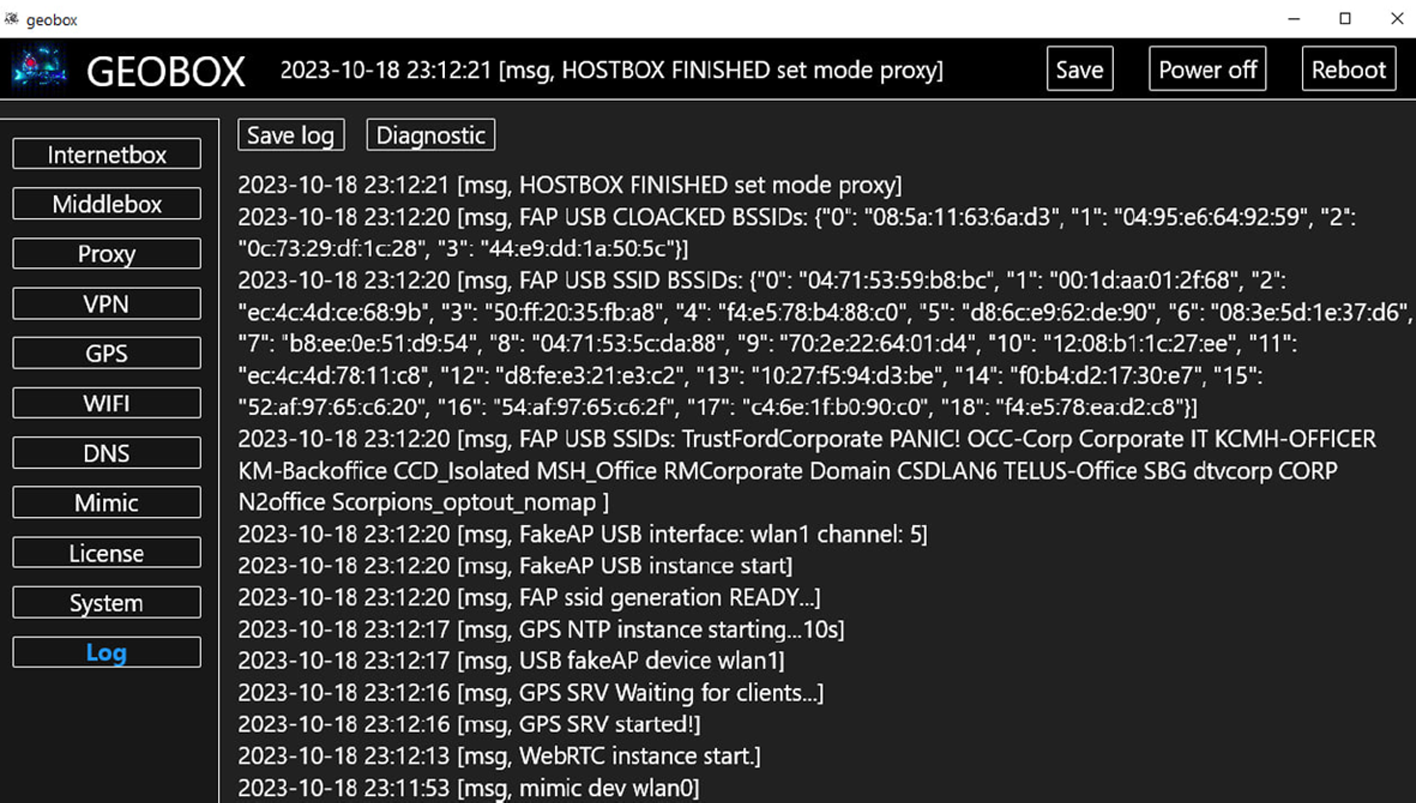
Resecurity lists the following main capabilities:
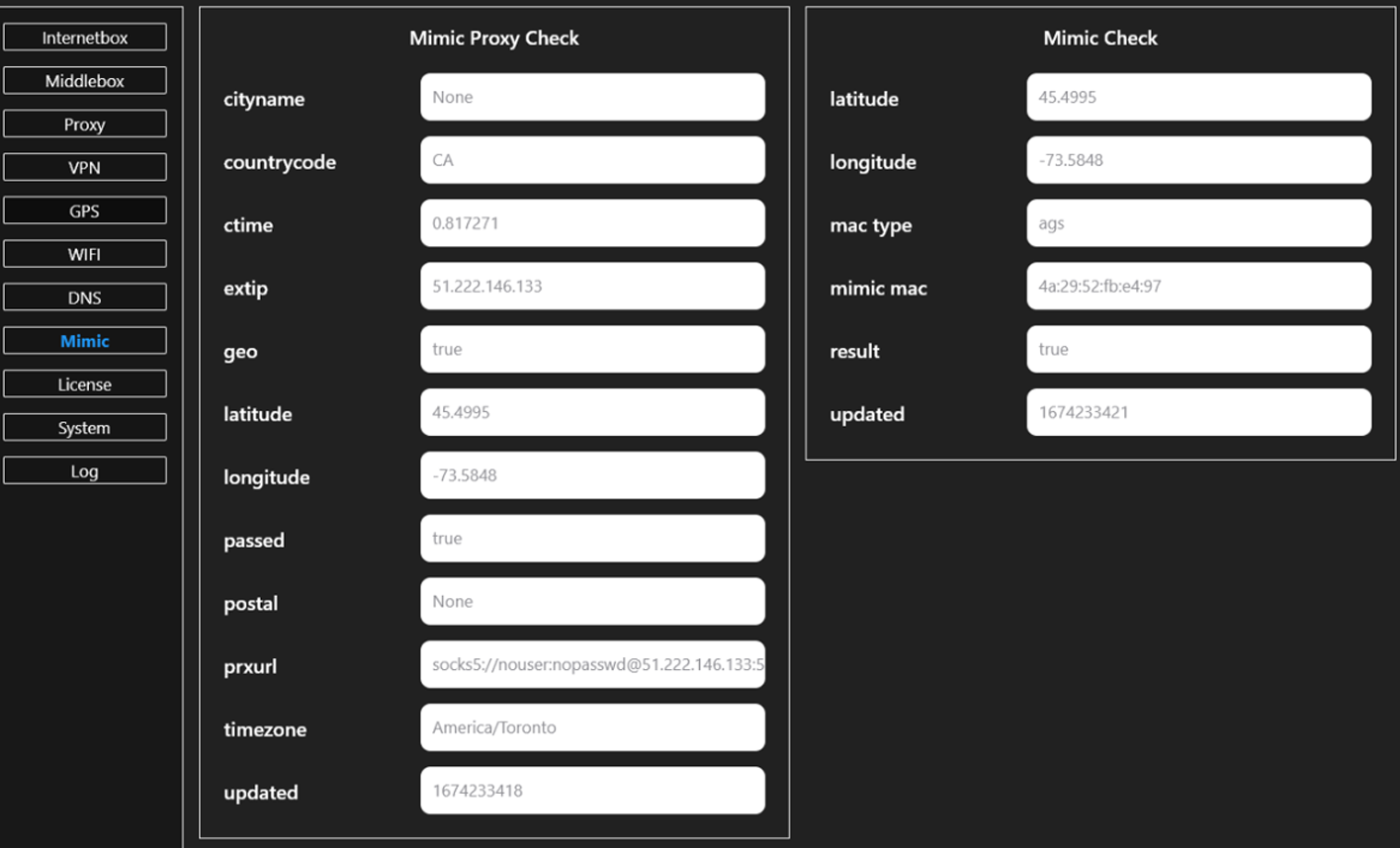
- GPS spoofing even on devices without a receiver, allowing users to fake their geographic location and bypass location-based security or engage in location-specific fraud.
- Emulates specific network settings and Wi-Fi access points to disguise illicit activities as legitimate network traffic.
- Anti-fraud circumvention to support activities like financial fraud and identity theft.
- Routing traffic through anonymizing proxies to obfuscate the threat actor's location.
- WebRTC IP masking and Wi-Fi MAC Address masquerading to hide the user's real IP address and mimic Wi-Fi network identifiers, complicating digital footprint tracking.
- Extensive support for VPN protocols, including DNS configurations for specific locations to prevent data leaks.
- Support for LTE modems for mobile internet connectivity, adding another layer of anonymity.
The most enticing part is that the above tools are packaged in a user-friendly environment that is easy to use even by low-skilled threat actors, who are given clear and detailed instructions in the accompanying user manual.
Source: Resecurity
Resecurity believes that GEOBOX can enable a broad spectrum of cybercrimes, primarily helping users remain anonymous and hard to trace.
Examples include cyberattack coordination, darknet market operation or access, financial fraud, credential stuffing, malware distribution, and disinformation campaigns.
Although GEOBOX doesn't introduce any functionality that is not already available in standalone tools or specialized Linux distros, like Kali Linux, its comprehensive and user-friendly suite makes it ideal for users looking to swiftly deploy new, disposable hacking devices.
Furthermore, its accessibility and ease of use make it particularly attractive to novice or low-skilled cybercriminals venturing into the space for the first time.
.jpg)

Comments
Hydranix - 1 month ago
There's nothing particularly alarming about this toolkit from what I can see.
Most of the features it offers are commonly used by privacy-minded normal everyday internet users. Hell, im sure we all used a GPS spoofer(Pokémon?)...
This article is making this thing seem.like it can hack ATMs or sniff your debit card at the liquor store. Those last two things do exist and deserve more attention than an overpriced RPi OS marketed.towards unintelligent criminals who can't grasp kali and think this device is their golden ticket.
electrolite - 1 month ago
The way this article is framed leaves a lot more to be desired. Oh my god, with this $700 and I can be a hacker. Just look at the interface. The user would need to have some knowledge of networking to use it i.e. this is not for neophytes.
"WebRTC IP masking and Wi-Fi MAC Address masquerading to hide the user's real IP address and mimic Wi-Fi network identifiers, complicating digital footprint tracking."
Oh my god, i am masking my webRTC IP. Any user who gives a hoot about privacy would want to mask that. Wi-Fi MAC address masquerading, you can do that on Windows with most Wifi adapters.
This article would have been so much better if this article was about GEOBOX capabilities, and leave the fear mongering and stop trying to frame the Raspberry Pi as criminal accessory. And I thought the article about the Flipper zero was bad.