
Today, Palo Alto Networks warns that an unpatched critical command injection vulnerability in its PAN-OS firewall is being actively exploited in attacks.
"Palo Alto Networks is aware of a limited number of attacks that leverage the exploitation of this vulnerability," warns the Palo Alto security bulletin.
The flaw, which has been discovered by Volexity and is tracked as CVE-2024-3400, is a command injection vulnerability that received the maximum severity score of 10.0 as it requires no special privileges or user interaction to exploit.
The vendor clarified that the issue affects specific versions of PAN-OS software when both the GlobalProtect gateway and device telemetry features are enabled.
"A command injection vulnerability in the GlobalProtect feature of Palo Alto Networks PAN-OS software for specific PAN-OS versions and distinct feature configurations may enable an unauthenticated attacker to execute arbitrary code with root privileges on the firewall," explains the Palo Alto Networks advisory.
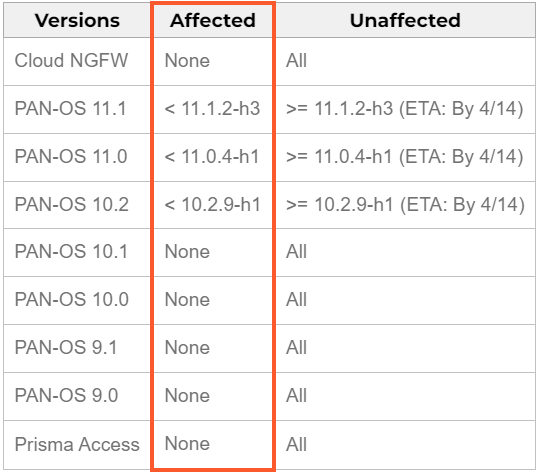
The vulnerable versions are PAN-OS 10.2, 11.0, and 11.1, and fixes for these versions are expected by April 14, 2024. The vendor will implement hotfixes by Sunday with the release of the following versions:
- PAN-OS 10.2.9-h1
- PAN-OS 11.0.4-h1
- PAN-OS 11.1.2-h3
Products like Cloud NGFW, Panorama appliances, and Prisma Access are not affected. An overview of the impact can be seen in the table below:
Threat researcher Yutaka Sejiyama reported on X that his scans show there are currently 82,000 exposed devices online that might be vulnerable to CVE-2024-34000, with 40% residing in the United States.
BleepingComputer contacted Volexity and Palo Alto Networks with questions on how the zero-day is being exploited.
Mitigating CVE-2024-3400
Since CVE-2024-3400 is already under active exploitation, impacted users must apply mitigations immediately to address the risk until security updates are available.
The advisory proposes implementing the following measures:
- Users with an active 'Threat Prevention' subscription can block attacks by activating 'Threat ID 95187' in their system.
- Ensure that vulnerability protection is configured on 'GlobalProtect Interfaces' to prevent exploitation. More info on that is available here.
- Disable device telemetry until fixing patches are applied. Instructions on how to do that can be found on this webpage.
Palo Alto Networks devices often become targets of sophisticated threat actors due to their deployment in corporate networks.
In August 2022, hackers exploited another zero-day in PAN-OS to carry out amplified TCP denial-of-service (DoS) attacks.
This time, the issue is much more severe, and its exploitation would be far more damaging to the targets, so admins must take prompt action to secure their systems.
Update 4/12 - CISA has added CVE-2024-3400 onto its Known Exploited Vulnerabilities (KEV) catalog, setting the patching deadline for federal agencies to April 19, 2024.
Update 4/16 - Palo Alto Networks updated their advisory today to warn that the previously shared mitigations of disabling device telemetry have been found to be ineffective at protecting devices.
Therefore, the best solution is to install the latest PAN-OS software update to fix the vulnerability.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now