“He who controls the spice controls the universe.” – Frank Herbert, from the Dune series
Shawn Helton
21st Century Wire
Over the past week, much of the CIA’s cyber hacking capabilities were allegedly laid bare by the Wikileaks ‘Vault 7’ publication. According to the transparency seeking website, they’ve published less than 1% of the intelligence regarding their Vault 7 series under the moniker Year Zero.
All in all, the Wikileaks Vault 7 release is said to be the largest publication of classified intelligence in history. While there are still many unknowns associated with this latest CIA centered leak, there are a quite a few things to consider.
Let’s explore some of what we know to date and how it relates to other suspicious tech related stories over the past few years…

‘YEAR ZERO – ZERO DAYS’ – Wikileaks discloses the CIA’s cyber hacking capabilities – still no official comment from the intelligence agency. (Photo Illustration 21WIRE’s Shawn Helton)
Wikileaks ‘Vault 7’
In 21WIRE‘s first report regarding the new revelations concerning Wikileaks Vault 7, we discussed how some of the content exposed in part one of Year Zero revealed what many in new media and other investigative fields have thought technologically possible for years.
Here’s a portion from the 21WIRE news alert mentioned above that describes the latest controversial publication by Wikileaks:
“WikiLeaks has released its largest ever publication of confidential documents on the Central Intelligence Agency. Entitled ‘Vault 7’ and containing a password that echoed the alleged JFK quote “splinter the CIA into a thousand pieces and scatter it into the winds,” this leak comprises 8,761 documents and files from an isolated, high-security network situated inside the CIA’s Center for Cyber Intelligence in Langley, Virginia.
‘Year Zero’, which is part one of the leak and conveniently named after a ‘zero day’ exploit used by intelligence agencies, was gathered throughout 2016 and is said to be the ‘largest intelligence publication in history’.
 Whilst a lot of the information and methodology outlined in ‘Year Zero’ is of no surprise to security analysts and researchers since the Edward Snowden (image, left) revelations, once again the public has explicit confirmation of how one of the most powerful intelligence agencies in the world, aided by their international counterparts like GCHQ, have been infiltrating and scooping vast quantities of private information from Apple and Android devices right up to Samsung ‘Smart TV’ technology where false ‘stand-by’ modes and live microphones can be executed to record information and send it back to the appropriate servers.”
Whilst a lot of the information and methodology outlined in ‘Year Zero’ is of no surprise to security analysts and researchers since the Edward Snowden (image, left) revelations, once again the public has explicit confirmation of how one of the most powerful intelligence agencies in the world, aided by their international counterparts like GCHQ, have been infiltrating and scooping vast quantities of private information from Apple and Android devices right up to Samsung ‘Smart TV’ technology where false ‘stand-by’ modes and live microphones can be executed to record information and send it back to the appropriate servers.”
The ‘Year Zero’ leaks a simple but cleaver play on the term zero day – something which is defined on Wikipedia as an “…undisclosed computer-software vulnerability that hackers can exploit to adversely affect computer programs, data, additional computers or a network.” A zero day, zero hour exploit is said to leave a software author without the necessary time to correct coding or “workaround” actions of a particular hack or intrusive malware damage.

(Image Source: daily express)
According to Wikileaks and its editor-in-chief Julian Assange, their most recent ‘treasure trove’ of confidential files were obtained by a current or former CIA contractor, a story similar in scope and impact to the collection of documents dropped by former CIA/NSA contractor Edward Snowden but are said to be much larger.
This time, the public has been given a glance inside the prism of the CIA’s cyber hacking potential and data mining efforts similar to the NSA.
In May of 2013, Snowden revealed information displaying that American citizens as well as other foreign nations throughout the world were subject to unprecedented levels of spying at the behest of the NSA. Massive data mining via XKeyScore and other similar applications proved to be very controversial particularly in America – as it seemed to be in direct contradiction to the US Constitution’s 4th Amendment.
Over the past decade other aspects of NSA spying activities were revealed under the George W Bush administration in 2005 and further brought to light by Mark Klein, a former AT&T technician who exposed how the multinational telecommunications company was working with the intelligence community to collect the public’s data.
In 2011, Gadgets and Gizmos reported the following:
“The recent Web 2.0 2011 conference in San Francisco saw the issue made public and now the worry is that private information could be obtained by third parties using this secretly stored data.
Once the data is accessed it can even be downloaded onto an interactive map which shows where the owner of the device has been lately. So far the best way to avoid this causing a problem is to go into the settings menu and turn of the location services all together.”
The newly leaked Vault 7 documents identify specific cyber weapons, hacking systems, viruses and malware created by the CIA that can be used on just about anyone or any entity. This most assuredly will cause other countries to become more critical of the agency’s cyber capabilities. By the looks of it, this is something that appears to be happening in Germany, as the Wikileaks docu-dump exposed an apparent CIA spy-hub in Frankfurt.
Zero Hedge reports:
“The consulate was the focus of a German investigation into US intelligence capabilities following the 2013 revelation that NSA agents had tapped Chancellor Angela Merkel’s phone.
German daily “Süddeutsche Zeitung” reported the building was known to be home to a vast network of intelligence personnel including CIA agents, NSA spies, military secret service personnel, Department of Homeland Security employees and Secret Service employees. It reported the Americans had also established a dense network of outposts and shell companies in Frankfurt.”
Germany’s reaction could prove to be more theatrical than that of true concern – only time will tell.
If Vault 7 is to be accepted wholesale, it also reveals that since the 9/11 attacks “…the CIA has gained political and budgetary preeminence over the U.S. National Security Agency (NSA). The CIA found itself building not just its now infamous drone fleet, but a very different type of covert, globe-spanning force — its own substantial fleet of hackers.” Part and parcel to this, Wikileaks contends that CIA hackers have developed cyber weaponry to spy on people through cell phones, computers and smart TVs.
According to ‘Year Zero’ part one of the Wikileaks Vault 7 release:
“The increasing sophistication of surveillance techniques has drawn comparisons with George Orwell’s 1984, but “Weeping Angel”, developed by the CIA’s Embedded Devices Branch (EDB), which infests smart TVs, transforming them into covert microphones, is surely its most emblematic realization.
The attack against Samsung smart TVs was developed in cooperation with the United Kingdom’s MI5/BTSS. After infestation, Weeping Angel places the target TV in a ‘Fake-Off’ mode, so that the owner falsely believes the TV is off when it is on. In ‘Fake-Off’ mode the TV operates as a bug, recording conversations in the room and sending them over the Internet to a covert CIA server.”
Interestingly, Wikileaks published a batch of classified CIA spy/hacking documents that not only include the privacy invading ‘Weeping Angel‘ developed by the clandestine agency to listen on microphones covertly but also ways the CIA has sought to remotely “infect and control Microsoft Windows,” with viruses like ‘Hammer Drill‘ as well as “automated infestation and control of CIA malware, such as “Assassin” and “Medusa.”
According to security analysts, the CIA has designed the covert methods listed above for hostile foreign actors. However, since the intelligence service has had a propensity of going rogue, these technological leaps made by the secretive agency should be a major concern to the general public.
Over the past few decades there have been other spoken critics of intelligence services such as well-known journalist James Bamford and former high-ranking NSA official William Binney, both who have come forward to share the inner workings of the security world.
The screenshot above from Wikileaks Vault 7 discusses CIA’s techniques that can be used to frame other entities for a malware attack.
Framing the Big Bear?
One of the more curious details contained in Vault 7 were the revelations concerning the CIA’s ability to mask any hacking fingerprints that could potentially implicate the agency. Additionally, the secretive agency could also leave behind potential evidence that a cyber attack was carried out by a foreign body or nation. Here’s another passage from the Wikileaks publication on the matter:
““Tradecraft DO’s and DON’Ts” contains CIA rules on how its malware should be written to avoid fingerprints implicating the “CIA, US government, or its witting partner companies” in “forensic review”. “
QUESTION: Is it possible that the CIA could use its highly specialized malware to frame a foreign country for violating US national security?
Zero Hedge reported the following Wikileaks information concerning the CIA’s ability to bypass device encryption before it can be applied as well as mask itself from forensic review via its own entity, the Center For Cyber Inteliigence (CCI):
Among the more notable disclosures which, if confirmed, “would rock the technology world“, the CIA had managed to bypass encryption on popular phone and messaging services such as Signal, WhatsApp and Telegram. According to the statement from WikiLeaks, government hackers can penetrate Android phones and collect “audio and message traffic before encryption is applied.”
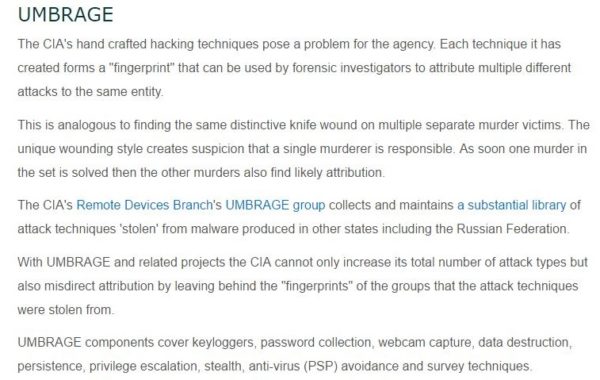
Another profound revelation is that the CIA can engage in “false flag” cyberattacks which portray Russia as the assailant. Discussing the CIA’s Remote Devices Branch’s UMBRAGE group, Wikileaks’ source notes that it “collects and maintains a substantial library of attack techniques ‘stolen’ from malware produced in other states including the Russian Federation.”
Here’s an image originally published by Wikileaks Vault 7 that displays the CIA’s Center For Cyber Intelligence apparatus…

With claims of alleged Russian hacking at the forefront of Western intelligence, let’s take another look at how that meme started…
Prior to the 2016 US presidential race taking place the mainstream media along with the White House, set the stage for a massive PR push implicating Russia as a disrupting force for democracy – allegedly through Kremlin-sponsored hacking of US democratic institutions and through ‘sophisticated Russian propaganda.’
In August, the western media’s claims against Russia began to hit overdrive, when the “New York Times’s Moscow bureau was the target of an attempted cyber attack this month. But so far, there is no evidence that the hackers, believed to be Russian, were successful.”
Flash forward to September here and here, as well as early October in the lead up to President Obama’s Russian Hack decree, the Clinton-friendly outlet, the NY Times, had all but solidified the Russian cyber-hack claims – but once again, without any definitive evidence or proof.
Throw in another American ‘October surprise’ in the form distributed denial of service (DDoS) attacks, renewed calls for the Stop Online Piracy Act (SOPA) internet, led to so-called cyber experts blaming the largest ‘hack on America’ because of the inability to pass SOPA – in effect, reigniting the previously stalled SOPA in Washington DC, along with all of its draconian copyright law positions – all perfectly timed as mainstream reports regarding fake news suddenly became all the rage across all forms of media.
Will Vault 7 prove to shed light on other CIA related activities?

The screenshot above from Wikileaks Vault 7 discusses the CIA’S HIVE multi-platform software control system.
DDoS Attacks
In October of 2016, I noted some of the suspicious activity surrounding America’s biggest distributed denial of service (DDoS) attack that was said to be caused by the malware Mirai. Given that there was a ‘hardcoded blacklist’ of certain government entities and major multinational companies/defense contractors from being attacked – its seems more likely that the attack was US government created:
“Interestingly, according to Bradley Barth, a senior reporter for the IT security online magazine SC, the Mirai (supposedly leaked on September 30th) contains a very unique subset of characteristics that will not attack certain IP addresses such as the Department of Defense (DoD), the US Postal Service and consumer giant General Electric (GE) due to its coding:
“An Imperva analysis of the source code revealed several unique traits, including a hardcoded blacklist of IPs that the adversary did not want to attack, perhaps in order to keep a low profile. Some of these IPs belonged to the Department of Defense, the U.S. Postal Service and General Electric (GE).”
Though SC claims that the makers of Mirai may have been trying to keep a low profile, the recent DDoS attack attributed to the malware was as high-profile as you can get – so this begs the question, what was the real reason the malware creators put an IP blockade on the DoD, the Postal Service and GE?”
Is it possible that the DDoS attack originated from whitehat hackers associated with the US government, a major US defense contractor like GE or some other intelligence service, possibly the CIA?

‘HACKED?’ – Michael Hastings death sparked a wave of controversial theories. (Image source: pinterest)
CIA Hacking Tools
Upon closer inspection of the Wikileaks Vault 7 release, we see that in addition to the public’s privacy apparently being invaded through the CIA’s ability to bypass encryption on Android and iOS phones, computers and smart TVs – there was also the Wikileaks revelations exposing the agency’s development of vehicular control.
Wikileaks Vault 7 stated the following stunning revelation:
“As of October 2014 the CIA was also looking at infecting the vehicle control systems used by modern cars and trucks. The purpose of such control is not specified, but it would permit the CIA to engage in nearly undetectable assassinations.”
It is this part of Year Zero that has revived the conspiracy surrounding the death of investigative reporter and war veteran Michael Hastings, who died after his Mercedes C250 coupe supposedly “burst into a giant fireball in the early hours of June 18 2013.” According to eyewitness accounts, Hastings was going at a high rate of speed as “sparks and flames” were seen before his fiery automobile crashed.
The UK’s Sun recently revisited the Hastings tragedy. Here’s a passage of that report:
“Hastings – a vocal critic of government mass surveillance – had sent an email to colleagues and friends just 12 hours earlier, telling them he was onto a “big story” and was under investigation.
The Buzzfeed and Rolling Stone contributor, 33, wrote: “The Feds are interviewing my ‘close friends and associates’.”
“May be wise to immediately request legal counsel before any conversations or interviews about our news-gathering practices.
“I’m onto a big story and need to go off the radar for a bit.”
WikiLeaks also tweeted after the crash to say Hastings had contacted its lawyer Jennifer Robinson just before his death, claiming the FBI was investigating him.
The FBI took a “departure from normal policy” to deny that Hastings had ever been under investigation after receiving a barrage of calls about his death.”
The CIA has failed to confirm or deny the authenticity of the Vault 7 release, only deepening the mystery surrounding the death of Hastings.
The question of CIA control over cars and trucks naturally leads us to what was revealed regarding high-tech avionics in recent years…

(Photo Illustration 21WIRE’s Shawn Helton)
Uninterruptible Flight Control
In my article entitled “FLIGHT CONTROL: Boeing’s ‘Uninterruptible Autopilot System’, Drones & Remote Hijacking,” I noted the CIA’s involvement in certain advancements in flight technology. Lets revisit a portion of that article describing the agency’s involvement:
“On December 4th of 2006, it was announced that Boeing had won a patent on an uninterruptible autopilot system for use in commercial aircraft. This was the first public acknowledgment by Boeing about the existence of such an autopilot system.
The new autopilot patent was reported by John Croft for Flight Global, with the news piece subsequently linked by a Homeland Security News Wire and other British publications around the same time. According to the DHS release, it was disclosed that “dedicated electrical circuits” within an onboard flight system could control a plane without the need of pilots, stating that the advanced avionics would fly the aircraft remotely, independently of those operating the plane:
“The “uninterruptible” autopilot would be activated – either by pilots, by onboard sensors, or even remotely via radio or satellite links by government agencies like the Central Intelligence Agency, if terrorists attempt to gain control of a flight deck.”
Continuing, I outlined the suspicious nature of both the MH370 disaster and that of MH17. Since then there have been a number of strange airline catastrophes including Germanwings 9525 and EygptAir MS804.
“Following the apparent ‘vanishing act’ of Malaysian Airlines flight MH370, many investigators and researchers began to question the likelihood of such an event happening in today’s high-tech world.
At 21WIRE, we’ve also looked into the unprecedented disappearance of MH370 and the subsequent downing of MH17, as certain details came to light regarding the history of the remote autopilot function installed within Boeing commercial airliners (a subject which also opens the door to the events of 9/11).
The Boeing 777 along with other Boeing models, can in fact be flown remotely through the use of independent embedded software and satellite communication. Once this advanced system is engaged, it can disallow any pilot or potential hijacker from controlling a plane, as the rooted setup uses digital signals that communicate with air traffic control, satellite links, as well as other government entities for the remainder of a flight’s journey.
This technology is known as the Boeing Honeywell ‘Uninterruptible’ Autopilot System.“
Has the CIA had the ability to remotely hack vehicles for much longer than we think?
The Wikileaks release once again opens questions about 9/11, the deep state and what intelligence agencies have control over in the War on Terror era.

‘CLOAKED’ – What other blueprints will Wikileaks provide regarding the CIA’s capabilities? (Image Source: offgraun)
Public Privacy Vs. the ‘Deep State’
In an article detailing the encryption saga between Apple and the FBI, we stated that there are no guarantees in the security world, especially if a digital master-key were to be created, as this would potentially make it easier for invaders (either the government, or various hackers) mining for data moving forward into the future.
If the CIA has been secretly data mining just like the NSA, they have unquestionably violated the public’s constitutional rights and trust.
Is this really what the CIA has been up too?
In a 2016 the Guardian interviewed some of those involved in the technology and security sector. These individuals offered their thoughts regarding the government’s continued encroachment on individual privacy. here’s another look at that passage:
Dan Kaminsky, the security expert who made his name with the discovery that one of the most basic parts of the internet, the domain name system, was vulnerable to fraud – disagrees: “Feds want final authority on engineering decisions, and their interests don’t even align with fighting the vast bulk of real-world crime.”
Continuing, The Guardian interviewed former FBI agent Michael German, currently the Brennan Center, a judicial think-tank. The following is a part of that interview:
“After 9/11, you had this concept of total information awareness. The intelligence community was very enamoured of the idea that all information was available. Much like the NSA, they wanted to see it all, collect it all, and analyse it all.”
Western political leaders and their media arms often discuss the dangers of so-called terror ‘sleeper cells’ residing in a nation near you, but none of them acknowledge or attempt to explain the historical fact that for decades, they themselves have helped to harbor, grow, foment and radicalize individuals through their own clandestine ‘counter-terrorism’ operations.
Many of these operations have directly implicated security agencies (and military alliances) such as the FBI, CIA, MI5, MI6 and NATO – in the production of real terror.
While most of these counter intelligence operations have fallen under the umbrella of the so-called War On Terror era, they have also largely served to obfuscate the nature of various government programs that some critics suggest is the work of a ‘deep state’ apparatus.
QUESTION: Will there be a large public outcry regarding the lack of oversight over the CIA’s spying and hacking capabilities?
Watch below as 21WIRE’s Patrick Henningsen discusses the ‘NSA-like body’ of the CIA on Peter Lavelle’s Cross Talk show on RT…
In Summary
The timely release of Vault 7 comes amid a flurry of wiretapping claims from President Donald Trump, while a review of US cyber capabilities and vulnerabilities is currently underway.
Additionally, the Wikileaks Vault 7 publication revealed the following stunning information concerning the scope of the CIA’s cyber capabilities previously unknown to the public:
“By the end of 2016, the CIA’s hacking division, which formally falls under the agency’s Center for Cyber Intelligence (CCI), had over 5000 registered users and had produced more than a thousand hacking systems, trojans, viruses, and other “weaponized” malware. Such is the scale of the CIA’s undertaking that by 2016, its hackers had utilized more code than that used to run Facebook. The CIA had created, in effect, its “own NSA” with even less accountability and without publicly answering the question as to whether such a massive budgetary spend on duplicating the capacities of a rival agency could be justified.”
In 2012, then CIA Director David Petraeus, “mused about the emergence of an “Internet of Things” — that is, wired devices — at a summit for In-Q-Tel, the CIA’s venture capital firm.”
The Wired magazine article continued, disclosing that the future of spying hinged on smart devices and a smart home:
“All those new online devices are a treasure trove of data if you’re a “person of interest” to the spy community. Once upon a time, spies had to place a bug in your chandelier to hear your conversation. With the rise of the “smart home,” you’d be sending tagged, geolocated data that a spy agency can intercept in real time when you use the lighting app on your phone to adjust your living room’s ambiance.”
The public has long been prepped for the surreal level of surveillance we are only just beginning to understand, whether through books, film or tech magazines or by the government itself – the warning signs of lost privacy and protection have been hidden in plain sight for decades.
Even still, Wikileaks Vault 7 shocks the avid researcher, writer and pundit as it gives further insight into the CIA’s multi-pronged ability to distort the perception of the public, while vacuuming up all kinds of data.
***
Author Shawn Helton is Associate Editor of 21st Century Wire, as well as an independent media forensic analyst specializing in criminal investigations and media coverage from war theaters.
READ MORE WIKILEAKS NEWS AT: 21st Century Wire WikiLeaks Files
SUPPORT OUR WORK BY SUBSCRIBING & BECOMING A MEMBER @21WIRE.TV