
The GandCrab ransomware TOR site allows shady data recovery companies to hide the actual ransom cost from victims and it is currently being disseminated through a large assortment of distribution channels according to a Coveware report.
Partnering with recovery firms who frequently access GandCrab's TOR site is an already documented feature, with "discount" codes being provided to the most active ones, usable when processing future settlements.
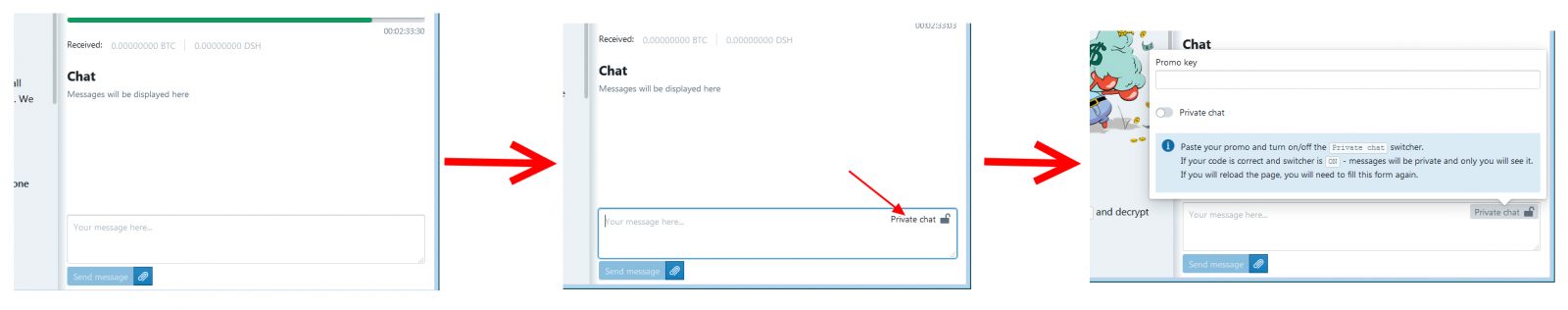
The ransomware's TOR site comes with a hidden private chat that can be enabled using one of the "discount" codes, allowing dishonest data recovery firms to hide the final cost of the GandCrab decryption process from its customers.
To enable the private chat GandCrab's TOR site, one has to follow this procedure:
- While in the plain chat, you click on the chat box and press SHIFT+CTRL+2
- Click on the Private link that appears in the chat box
- Enter promo code and slide the toggle, and, if the code is right, the chat will be tied to that promo code and can't be seen by the normal client
To enter the discount code you have to press Shift+Ctrl+1 keyboard combo, which will open a dialog box where the code can be entered. By following this procedure, recovery companies can reduce the price of the ransom amount by whatever discount, giving access to the victim to see one price, while the shardy recovery firm can pay a lower one.
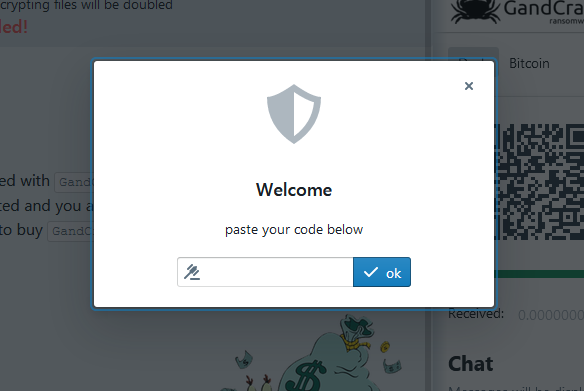
According to Coveware, "After entering the code, the applicable discount is displayed and the USD ransom amount on the payment pages is automatically adjusted. Discounts range from 5-20% depending on the size of the ransom."
Highly active ransomware with a RaaS "business" model
GandCrab was a very active ransomware strain all throughout 2018 as well as since the start of 2019, and it is known for requesting up to $3000 from its victims to decode encrypted files.
The GandCrab authors use a ransomware-as-a-service (RaaS) "business" model designed to make it simple for other threat actors to deploy it through their own malware campaigns for a share of the profit.
GandCrab is also known to use a large array of techniques for compromising its victims, via malvertising campaigns, by exploiting Struts, JBoss, Weblogic, and Apache Tomcat vulnerabilities, by camouflaging itself as an apparently harmless app or as a cracked utility, or even trying to brute force its way in when everything else fails.
Because GandCrab is distributed as part of a wide variety of exploit kits from RIG and GrandSoft to Fallout via automated malware campaigns, as well as in combination with other malware strains such as Emotet and Vidar, and this has as a direct result an increased number of ransom IDs being detected for each infection event.

As detailed by Coveware in their report:
Prior to the exploit kits gaining popularity, a single attack would typically have one or two unique IDs (file extensions). Each ID had its own TOR page, with a ransom amount scaled to the perceived value of the underlying machine. Since the more automated exploit kits have gained popularity, the number of unique IDs in a single infection has skyrocketed. Some victims have dozens of ID’s to contend with. Each ID tends to have the same ransom amount, indicating a ‘spray and pray’ methodology vs a more surgical attack.
Although a free decrypter for GandCrab was released by Bitdefender at the end of October, allowing victims to decrypt their locked files if they were affected by versions 1, 4 and 5 (up to v5.0.3) of the ransomware, there are no publicly available decryption tools for the latest versions of GandCrab starting with 5.0.4.
Protect yourself from ransomware
To protect your files from being encrypted by ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack. With a good backup, ransomware has no effect on you.
You should also have security software that incorporates behavioral detections to combat ransomware and not just signature detections or heuristics. For example, Emsisoft Anti-Malware and Malwarebytes Anti-Malware both contain behavioral detection that can prevent many, if not most, ransomware infections from encrypting a computer.
For a complete guide on ransomware protection, visit our How to Protect and Harden a Computer against Ransomware article.


Comments
Bullwinkle-J-Moose - 5 years ago
"With a good backup, ransomware has no effect on you."
-----------------------------------------------------------------------------------
Even with a good backup, ransomware does have an effect on you!
The time and aggravation, lost files, worrying that it will soon return
It's like when you google for the "highest quality" flashlight or "the brightest" flashlight and you get ten pages of results for Chinese garbage flashlights that are not worth a single dollar yet are being sold for $20 to pay for the google rankings just to sell that crap
or your wife buying 3 pizza cutters at the dollar store and each one breaks the first time you use it
It's not a deal, and I'm off topic but the aggravation and waste of time involved far exceeds just buying a single quality pizza cutter for $20 or $30 and handing it down to your grandchildren because it still works (No backup required)
Finding quality software is now impossible for the "average" consumer, and your infected backup will not help you
Thanks Google!
Bullwinkle-J-Moose - 5 years ago
Sorry, I was WAY off topic there
It's just the aggravation of dealing with this crap
It has an effect!