
South Korea has been blocking HTTP websites that are on their censor list for a while now and they have recently started using SNI filtering to block their counterparts served over HTTPS.
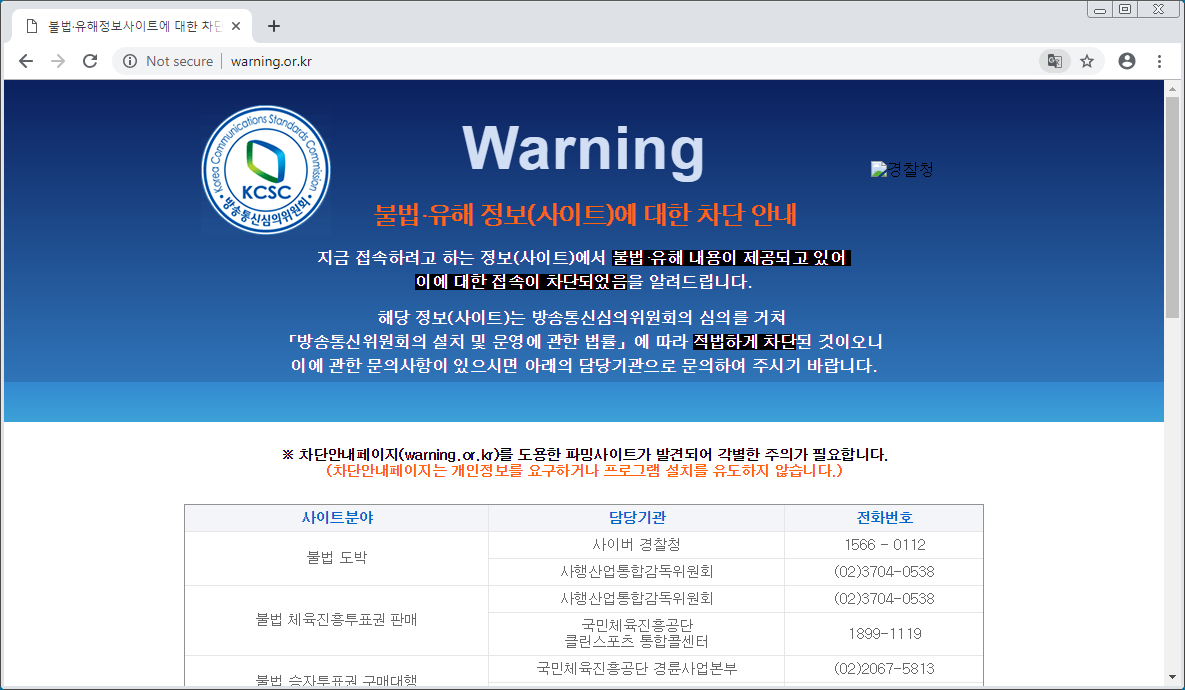
A warning page bearing the seals of the Korea Communications Standards Commission (KCSC) and the Korean National Police Agency is displayed for blocked HTTP websites, while TLS sites blocked using Server Name Indication (SNI) filtering will only throw a "This site can't be reached" error.
An OpenNet Initiative report from 2012 is still valid although quite dated given that the country has not updated its Internet surveillance approach since 2008, and it paints an accurate picture of the current state of Internet censorship in South Korea:
Despite the fact that South Korea has one of the most advanced information communication technology sectors in the world, online expression remains under the strict legal and technological control of the central government. The country is the global leader in Internet connectivity and speed, but its restrictions on what Internet users can access are substantial.
Also, Reporters Without Borders included South Korea on its list of countries "Under Surveillance" during 2011, and it also compared the level of Internet censorship to those experienced by citizens of Russia and Egypt in its "Enemies of the Internet" report, as described by The New York Times in 2012.
SNI filtering used to block websites
SNI is a TLS extension which allows browsers to inform a web server of the hostname they want to connect to at the beginning of the handshaking process, as detailed in IETF's RFC3546.
As reported by JoongAng Media Network Group's Lee Min Jung and other sources, South Korea has begun filtering the country's internet traffic to block TLS websites blacklisted by the KCSC.
Also, as Joseph Lorenzo Hall, the CTO of Center for Democracy & Technology (CDT), tweeted on February 12:
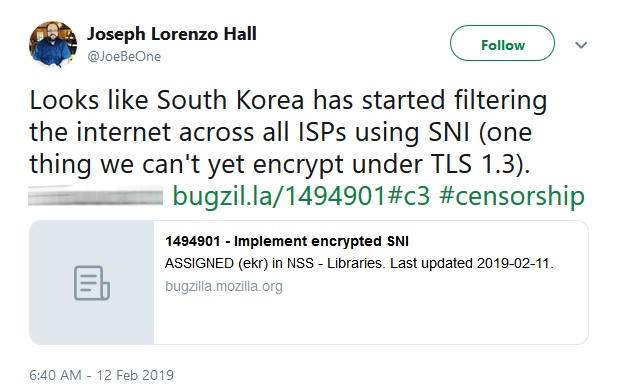
Hall told Bleeping Computer in an interview:
This is big on the censorship community as SNI blocking has been relatively rare... The ID we're working on will need to be updated to point to this as a definitive case: https://tools.ietf.org/html/draft-hall-censorship-tech-05.
Additionally, sources familiar with the matter told Bleeping Computer that researchers with probes in the country have been able to see SNI being used for filtering.
Bleeping Computer was able to verify the reports by connecting to some of the websites on KCSC's blacklist using a South Korean IP address.
While the block method used previously was based on DNS filtering according to South Korean media ("So far, the government has used DNS (Domain Name System) to block Internet addresses (URLs) of illegal harmful sites"), South Korea’s censoring technology now makes use of SNI filtering because the previous technique was easily bypassed using encrypted HTTPS connections.
SNI filtering is used when connecting to a website over HTTPS and it allows ISPs to inspect SNI packets sent by a user's browser to the server it wants to connect to during the authentication stage.
This is possible because while TLS 1.3 encrypts almost all the data sent between the client and the server, it will still allow ISPs to extract the domain name the client connects to as detailed in IETF's "Encrypted Server Name Indication for TLS 1.3" draft:
Although TLS 1.3 [RFC8446] encrypts most of the handshake, including the server certificate, there are several other channels that allow an on-path attacker to determine the domain name the client is trying to connect to, including:
- Cleartext client DNS queries.
- Visible server IP addresses, assuming the server is not doing domain-based virtual hosting.
- Cleartext Server Name Indication (SNI) [RFC6066] in ClientHello messages.
Right now, for HTTP connections, if the ISP detects one of the websites on KCSC's block list considered harmful, the user will be redirected to the warning page we mentioned in the beginning. On the other hand, if the website is rated as illegal or harmful, the contents will be completely blacked out.
On the other hand, when the browser connects via HTTPS, if the ISP detects one of the websites on KCSC's block list in the SNI authentication package, the website will be blocked and a "This site can't be reached" error will be displayed.
According to a tweet by Cloudfare's head of crypto Nick Sullivan, the South Korean government went one step further and decided to completely block all connections made using browsers that come with support for Encrypted SNI (ESNI) which would not allow it to snoop for the server names in the authentication packages sent to the websites' servers.
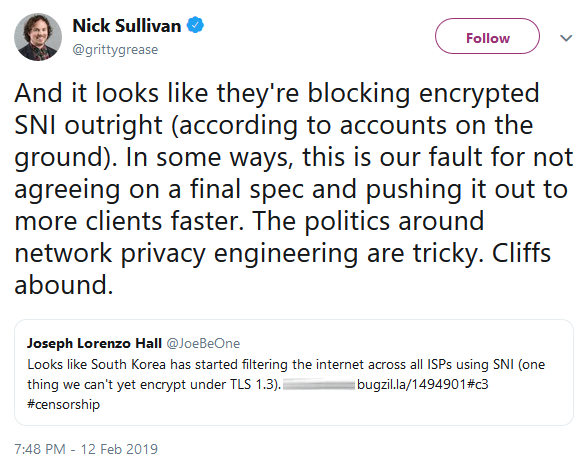
This is especially important if true because, once all connections will be made using ESNI, South Korea's KCSC will not be able to filter HTTPS traffic because it will have to block all websites served via ESNI-enabled servers.
Search engines also censored
As further detailed by Lee Min Jung, the SNI filtering was enabled on November 11, when some South Korean ISPs started blocking websites at the request of the authorities. However:
When this information became known, there was a controversy online. The opening of the packet is a criticism that it is not excessive surveillance or censorship. Especially, when adult videos, aka streaming sites are blocked, netizens are raising their voices, saying, "It is not private life censorship" and "What is different from China."
On the controversial date, the KCCA officially announced the ban on access to illegal foreign sites on the day, and decided to promote the public.
To add insult to injury, according to security researcher Pierre Kim, search engine results are also censored in South Korea:
Search engines are massively censored as well: Naver.com (first search engine in South Korea) and Google.co.kr will happily return 0 result about certain terms or will ask you information to release results (your name, your phone number, your birthday) saying that: "Harmful results for youth have been excluded. Users being more that 19 year-old can view all the results through the adult authentication."


Comments
Sheuk - 5 years ago
Seems that more and more countries are censoring the Internet now•••••••