There is much to be found online about recovering data from corrupt SD cards, but [StezStix Mix] had an entirely different problem with his card. He’d filmed an important video to it, then dropped it and ran his office chair over it, snapping it almost in half. He’s put up a couple of videos showing how he recovered the data, and we’ve put them below the break.
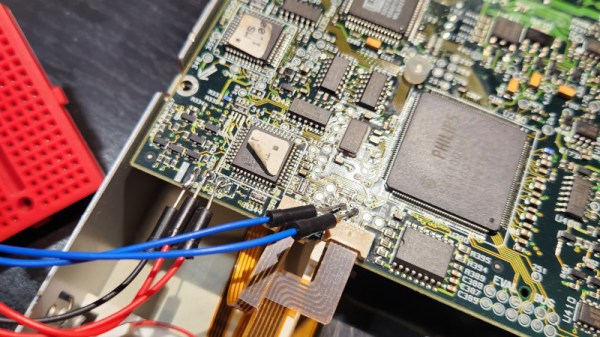
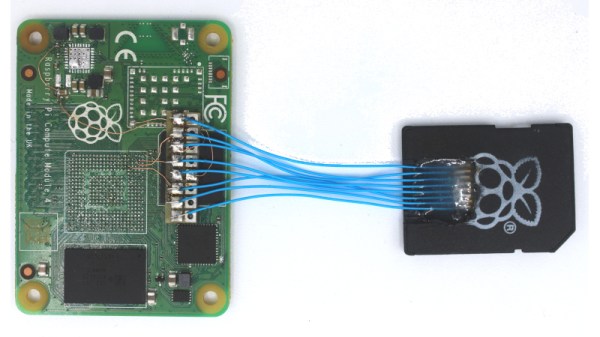
A modern SD card is mostly just plastic, as in the decades since the format was created, the size of the circuitry on it has decreased dramatically. So his stroke of luck was that the card circuitry was a tiny PCB little bigger than the contact pad area on a full size SD card. There was a problem though, it wouldn’t be easy to fit in an SD card socket. So in the first video he goes through physically wiring it to a USB card reader, which results in reading the data after a false start in remembering that an SD card activates a switch.
This however is not the end of the story, because he had viewers asking why he didn’t simply attach an SD card shaped bit of cardboard. So the second video below goes through this, trying both card, and an SD to micro SD adapter. We find that making something to fit an SD socket is a lot less easy than it looks, but eventually he manages it.
Meanwhile those of you with long memories may recall this isn’t the first SD surgery we’ve brought you.