 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A cybersecurity researcher has developed a new phishing technique that can bypass multifactor authentication and steal login cookies through Microsoft Corp.’s Edge WebView2.
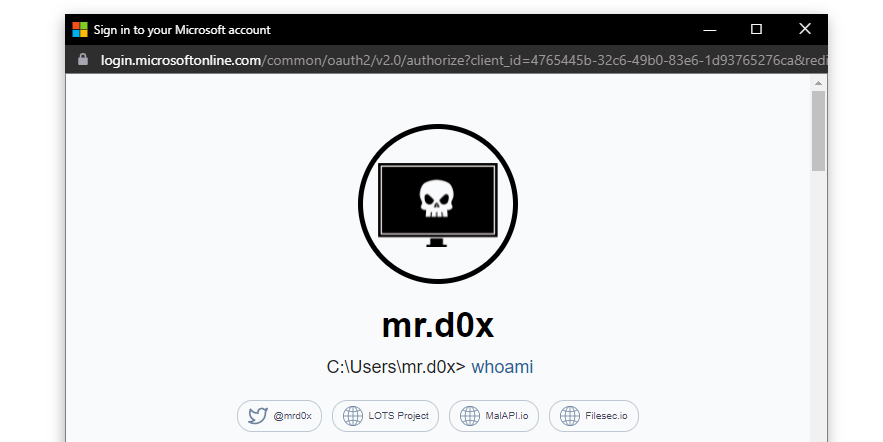
WebView2 is a runtime, or software and instructions that are executed while a program is running, that provides web-based features in Microsoft 365 desktop applications using Microsoft Edge as a rendering engine. As detailed June 21 by mr.d0x, the proof-of-concept phishing attack, dubbed “WebView2-Cookie-Stealer,” involves injecting malicious JavaScript code into websites loaded in an application that uses WebView 2.
In an example, mrd0x injected a JavaScript keylogger into a legitimate Microsoft login form that was loaded using WebView2. The page itself renders normally, but with the JavaScript running in the background, the code captures anything the user types in and sends it back to the designated web server.
The method does not stop at keylogging. Taking advantage of the way WebView2 accepts JavaScript, mrd0x was also able to steal any cookies sent by the remote server after a user logs in, including authentication codes.
Mrd0x also explains that WebView2 can be used to steal all available cookies for the current user in Google LLC’s Chrome. WebView2 allows an attacker to launch with an existing user date folder rather than creating a new one. The UDF contains all passwords, sessions and bookmarks relating to the user.
The methodology could be easily used to steal and import cookies using a simple Chrome extension such as “EditThisCookie,” Bleeping Computer reported Sunday. However, the more concerning aspect is that the attack methodology completely bypasses MFA, onetime passwords and security keys, since the cookies are stolen after the user is already logged in.
“This attack demonstrates that while useful, MFA is not a silver bullet against phishing attacks,” Erich Kron, security awareness advocate at security awareness training company KnowBe4 Inc., told SiliconANGLE. “Other precautions must be taken to secure accounts and protect organizations against attack.”
Kron explained that the attack relies on a human to take a dangerous action — executing a program downloaded from the internet — to begin its work. That makes it much less of a threat for the average user than one that requires a more easily disguised method. This particularly exposes people who download pirated software or game cheats.
“To protect against attacks such as this, having a policy against downloading or running unapproved software or browser add-ins, and educating users on the dangers of running this type of software, can have a significant reduction in risk for the organization,” Kron added.
THANK YOU