A cyber espionage operation known as the Naikon APT group attempted to install a backdoor on the computer of a staff member in the Western Australian Department of Premier and Cabinet, according to Check Point Research and the New York Times.
The security company released a new report on the Naikon APT group overnight and provided specific details of the threat to Australian government entities to the New York Times.
Naikon’s existence was first revealed by ThreatConnect and Defense Group back in 2015, but the group had been quiet since, “suggesting that they had either gone silent, increased their emphasis on stealth, or drastically changed their methodology of operations,” Check Point said.
Naikon’s current campaign started with the takeover of a diplomat’s computer.
“Our investigation started when we observed a malicious email sent from a government embassy in APAC to an Australian state government,” the security firm said.
The email contained an RTF file attachment, which had been weaponised by the attacker.
Citing Check Point, the New York Times report said the attacker “was able to take over the computer used by an Indonesian diplomat at the embassy in Canberra.”
“The hacker found a document that the diplomat was working on, completed it and then sent it to the staff member in the Western Australian [Department of Premier and Cabinet] office,” according to the news report.
Opening the altered document would lead to the installation of a backdoor called Aria-body that could be used to take control of a victim’s computer.
Check Point told the New York Times that the incident was discovered only because the hacker sent the email to a wrong address in the department, causing a bounceback.
“The transmission aroused suspicion that something in the original message was fishy, the authors of Check Point’s report wrote. That prompted the investigation that revealed the attempted attack - and its novel weapon,” reported the New York Times.
The incident occured on January 3, according to the newspaper.
iTnews has since confirmed that the New York Times confused the Premier's office with the Department of the Premier and Cabinet.
“There is no evidence the Premier’s office has been hacked," a state government spokesperson told iTnews.
“The malicious email referred to in the article was detected by the Department of the Premier and Cabinet’s email security and blocked. Thousands of malicious emails are blocked by the email security system every week.
“This demonstrates the Department has good protections in place, consistent with industry best practice.
“The incident was reviewed by the Australian Cyber Security Centre and the Department’s email security system. No further action was necessary.
Governments across APAC targeted
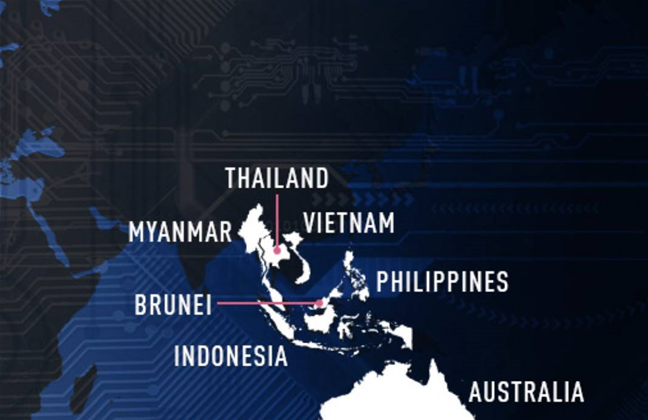
Check Point Research said that in addition to Australia, Naikon targeted “several national government entities” in Indonesia, the Philippines, Vietnam, Thailand, Myanmar and Brunei.
“The targeted government entities include ministries of foreign affairs, science and technology ministries, as well as government-owned companies,” it said.
“Interestingly, the group has been observed expanding its footholds on the various governments within APAC by launching attacks from one government entity that has already been breached, to try and infect another.”
Check Point said the attackers appeared to be after “specific documents from infected computers and networks within government departments”.
But, it said, they had also shown an interest in “extracting data from removable drives, taking screenshots and keylogging, and of course harvesting the stolen data for espionage.”
“If that wasn’t enough, to evade detection when accessing remote servers through sensitive governmental networks, the group compromised and used servers within the infected ministries as command and control servers to collect, relay and route the stolen data,” it added.
Updated, 9.35pm AEST: This article incorrectly stated the intended recipient of the email was in the WA Premier's office, citing Check Point and the New York Times. In fact, the target was in the Department of Premier and Cabinet. The article has been updated to reflect this.

















.png&h=141&w=208&c=1&s=1)

